Screenshots – There’s no metadata in a piece of paper!

Screenshots – There’s no metadata in a piece of paper!

By Matt Lashey | Head of Investigations
If screenshots are served as paper-based exhibits then how can we rely on them as being accurate without metadata?
My laptop delicately chimes as a new instruction drops into my inbox. “Images attached” the title reads. I glance down, the three letters I fear are starring back at me… PDF. I inhale with anticipation and reluctantly double-tap the trackpad. As suspected, ten pages of grayscale images that look like they arrived via a hand scanner attached to an Atari ST. If I squint a little and turn my head 90 degrees; they look a bit like text messages.
“We don’t agree that we sent these messages. Can you review the metadata of each photograph and provide a report dealing with their validity?”
Prior to issuing my standard response (can I have the images in the original format) and getting my standard answer (this is how they’ve been served by the prosecution) I decided to blog my frustrations. So, here it is…
Firstly, let me deal with what metadata is in a tech-friendly manner.
Metadata – in the most simplistic sense – is the information which sits behind a computer-generated file (digital document) and is not visible on the surface. For example, which profile was used to author/create the document, what type of document it is, which operating system and application was used to create it, along with numerous other additional pieces of information depending on the file type and the software used to create or modify it.
EXIF data is a type of metadata, provided within media files including photos (jpg, png, etc), videos (mp4, mov, etc), and audio (mp3, wav, etc).
For example; EXIF data in a photograph can contain such information as aperture, shutter speed, installed operating system, user profile details, device make/model, time/date the photo was taken and much more. If the device you’re using supports GPS (most current mobile phones with location services enabled), you can ascertain the location (latitude and longitude coordinates) of the device when the photograph was taken. See Fig 1:
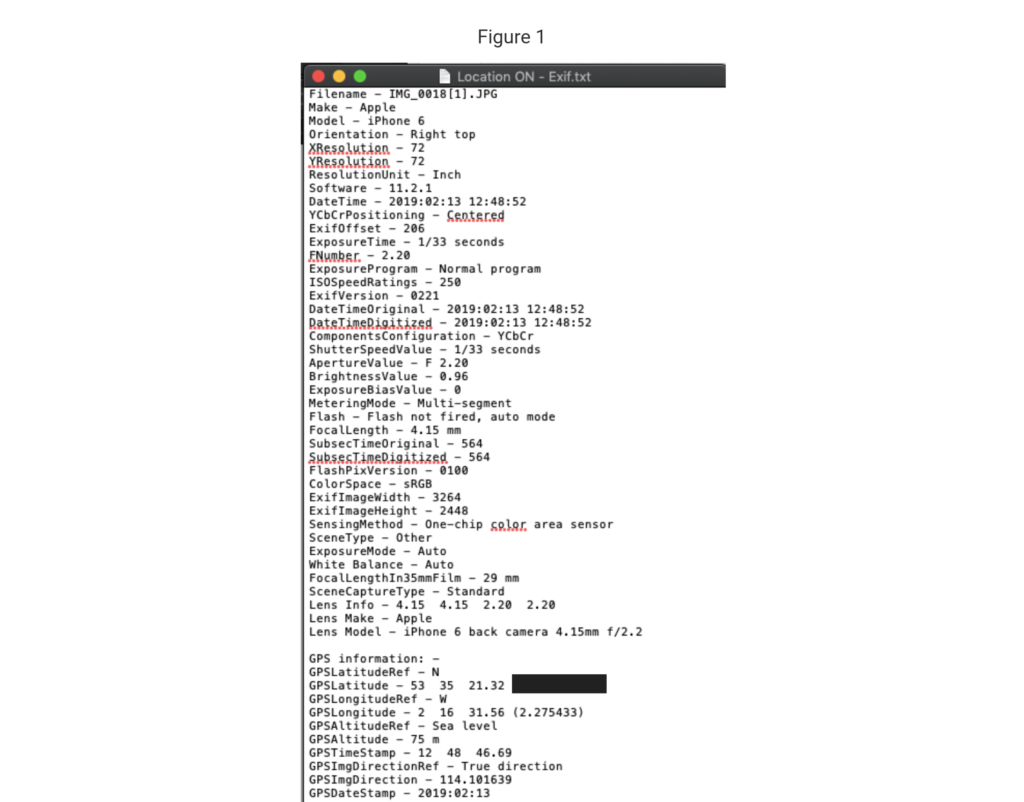
So, as you can imagine, this data can be extremely useful to a digital investigation. Being able to potentially pinpoint a mobile device when it took a photograph could prove critical when you’re assessing someone’s version of events. However, if you screenshot images, paste them onto a document and then print that document off, what you end up with is a piece of paper. A nicely exhibited piece of paper, but still a piece of paper. There’s no metadata in a piece of paper!
This issue becomes more significant when dealing with text messages (or any other kind of messages for that matter), due to how easy it is to fake them. Try it yourself; enter ‘fake message generator’ into a search engine of your choice now and see how many results you get. Type what you want and then customise the recipient, network, technology (2G, 3G or 4G), battery level, signal strength…the list goes on. When you’re happy, hit the ‘screenshot’ button and voila! Your fake text message is ready. See Fig 2 and 3:
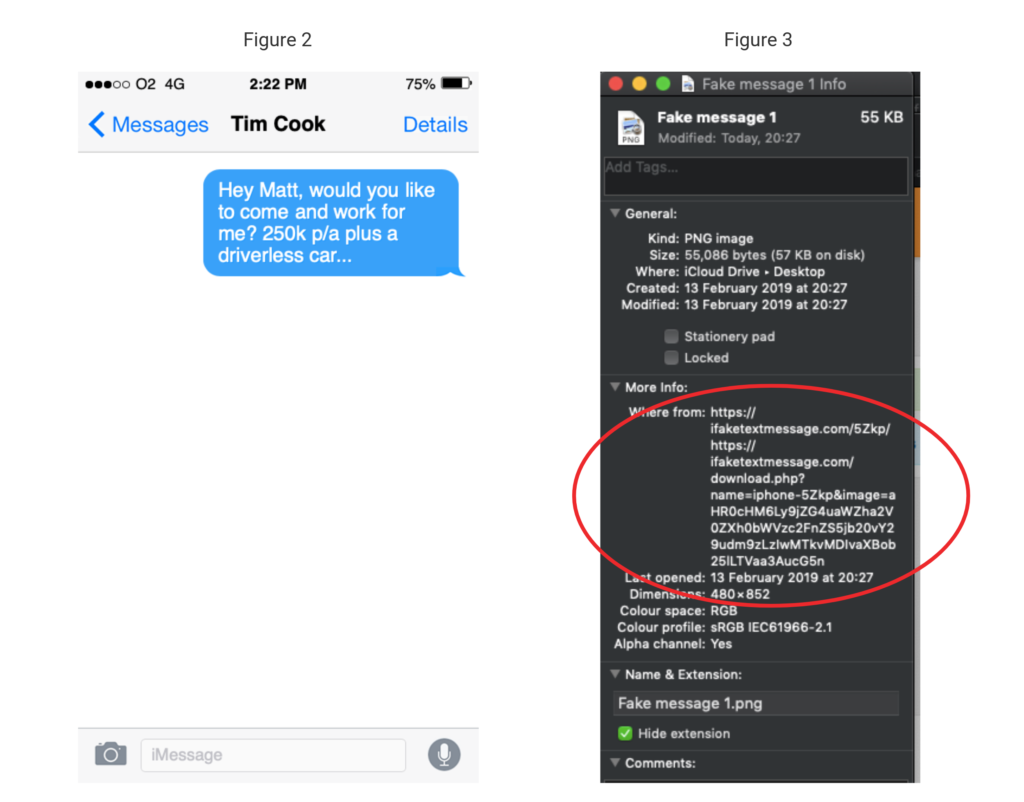
As you can see from Fig 3, if provided with the image in the correct format, I am able to view the metadata, or ‘properties’ in this example. This would enable me to conclude that the message was fake and that I’m not destined for a career at Apple. However, print this message off and photocopy it into a bundle of other paper-based exhibits and my findings become inconclusive.
In summary, if images or screenshots are served as a paper-based exhibits or their forensic integrity has not been maintained (copied and pasted into a document), then how can we rely on them as being accurate?
Call us today and speak with a Forensic Specialist
Send an enquiry to our experts
After submitting an enquiry, a member of our team will be in touch with you as soon as possible
Your information will only be used to contact you, and is lawfully in accordance with the General Data Protection Regulation (GDPR) act, 2018.