‘NotPetya’ cyber-attack hits international organisations

‘NotPetya’ cyber-attack hits international organisations

The ‘NotPetya’ cyber-attack affected a range of companies worldwide.
It has been suggested that this ‘NotPetya’ cyber-attack took advantage of similar weaknesses that were exploited by last month’s WannaCry attack.
The ransomware was initially called ‘Petya’ and the updated version Petrwrap, however Kaspersky Lab reported that it believed the malware was a “new ransomware that has not been seen before” despite its resemblance to ‘Petya’. As a result, they have dubbed this new virus ‘NotPetya’. The virus, the source of which is not yet known, freezes the user’s computer and demands an untraceable ransom be paid in the digital Bitcoin currency.
Who was affected?
The attack initially hit the Ukraine, affecting major firms, government systems, Kiev’s main airport and state banks. More worryingly the infamous Chernobyl nuclear power plant was also attacked, shutting down the automatic Windows based sensors and forcing the site to monitor radiation levels manually.
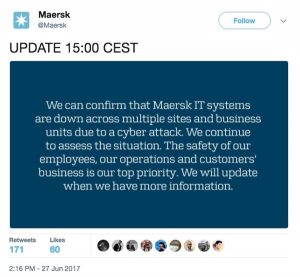
The attack then spread across Europe with Reuters reporting that Danish shipping giant A.P. Moller-Maersk was also affected by the cyber-attack, causing mass outages across its computer systems globally. Maersk handles one out of seven containers shipped globally and the breakdown affected all business operations, including container shipping, port and tug boat operations, oil and gas production, drilling services, and oil tankers. In the UK, advertising agency WPP was also attacked, with all its IT systems being shut down as a consequence.

The BBC has documented other large organisations that have been affected;
- Antonov: Russian aircraft manufacturer
- Rosneft: Russia’s biggest oil producer
- Heritage Valley Health System: Pennsylvania hospital operator, which reported its computer network was down, causing operations to be delayed – but it is not yet clear if it was subject to the same type of attack
- Mondelez: Spanish food giant – whose brands include Oreo and Toblerone – according to the country’s media. A Cadbury factory in Tasmania, Australia is affected
- TNT: The Netherlands-based shipping company, which said some of its systems needed “remediation”
- St Gobain: French construction materials company
- Merck: US pharmaceuticals-maker
- DLA Piper: International law firm – a sign in the firm’s Washington DC office said: “Please remove all laptops from docking stations and keep turned off – no exceptions.”
It has been reported that the malware appears to be spreading by exploiting the same loopholes within Windows systems, just as WannaCry did. These varying range of organisations have been hit due to not updating their security systems and applying the relevant software patches.
As we’ve mentioned before in our previous blog, companies that don’t adequately prepare themselves against a cyber-attack not only face a risk to their reputation and financial assets, but also expose themselves to fines, prosecution or civil proceedings if they are found to have been unprepared to respond to a cyber incident. This will be compounded by the looming GDPR, which takes effect on May 25th 2018.
Call us today and speak with a Forensic Specialist
Send an enquiry to our experts
After submitting an enquiry, a member of our team will be in touch with you as soon as possible
Your information will only be used to contact you, and is lawfully in accordance with the General Data Protection Regulation (GDPR) act, 2018.